System Center Updates Publisher (SCUP) is a very useful SCCM add-on for adding third party updates to Windows Server Update Services (WSUS). SCUP can add updates to WSUS from a variety of manufactures such as Adobe, Dell and HP.
On several occasions, we have integrated SCUP within SCCM in a client environment and found that SCCM fails to download the updates from WSUS. This typically occurs (but not limited to) when the below conditions are met:
- The SCCM Software Update Point is configured to download updates from the Microsoft over the internet,
- The SCCM Software Update Point is configured to use a web proxy server,
- The environments web proxy server is not configured to direct traffic intended for internal locations back internally.
When checking the patchdownloader.log within the SCCM site logs errors are reported such as:
<11-26-2019 21:11:19.079+00><thread=5952 (0x1740)> Contentsource = http://server1.local:8530/Content/83/0F4A1240F08D948AA1EBB603D3CECDABD2EB0483.cab . $$<Software Updates Patch Downloader> <11-26-2019 21:11:19.188+00><thread=5952 (0x1740)> Downloading content for ContentID = 16796176, FileName = AcroRdrDCUpd1901220036.cab. $$<Software Updates Patch Downloader> <11-26-2019 21:11:19.438+00><thread=5952 (0x1740)> Try username test\proxyuser $$<Software Updates Patch Downloader><11-26-2019 21:11:19.438+00><thread=19016 (0x4A48)> Proxy enabled proxy server proxy.internal:8080 $$<Software Updates Patch Downloader> <11-26-2019 21:11:19.438+00><thread=19016 (0x4A48)> Connecting - Adding file range by calling HttpAddRequestHeaders, range string = "Range: bytes=0-" $$<Software Updates Patch Downloader> <11-26-2019 21:11:19.438+00><thread=19016 (0x4A48)> HttpSendRequest failed 504 $$<Software Updates Patch Downloader> <01-24-2020 11:00:57.885+00><thread=9132 (0x23AC)> Contentsource = http://server2.local:8530/Content/49/FA296F5636F23107A3AF0EF1B4B7AFEDA8B94A49.cab . $$<Software Updates Patch Downloader><01-24-2020 11:00:57.886+00><thread=9132 (0x23AC)> Downloading content for ContentID = 16811947, FileName = AdbeRdrUpd11023.cab. $$<Software Updates Patch Downloader> <01-24-2020 11:00:57.887+00><thread=9132 (0x23AC)> Try username test\proxyuser $$<Software Updates Patch Downloader> <01-24-2020 11:00:57.911+00><thread=8376 (0x20B8)> Proxy enabled proxy server proxy.local:3128 $$<Software Updates Patch Downloader> <01-24-2020 11:00:57.912+00><thread=8376 (0x20B8)> HttpSendRequest failed 12002 $$<Software Updates Patch Downloader>
In general, the cause of this is that SCCM issending the request to download the update (added to WSUS by SCUP) to the web proxy which then fails because the internal location is not available on the public internet. What we want is for SCCM to bypass the proxy for internal addresses however the GUI contains no options for this or setting a bypass list.
The good news is that you can tell SCCM to bypass the proxy by amending an SCCM configuration file. We also suggest amending WSUS to configuration to keep things in sync. The two files you want to amend are:
C:\Program Files\Microsoft Configuration Manager\bin\X64\smsexec.exe.config
C:\Program Files\Update Services\Services\WSUSService.exe.config
Within these files add the below section and amend as per your environment:
<system.net> <defaultProxy> <proxy usesystemdefault = "false" proxyaddress= "http://proxy.local:8080" bypassonlocal= "true"/> <bypasslist> <add address="server1.local"/> </bypasslist> </defaultProxy> </system.net>
The next step is to remove the proxy configuration from within the SCCM GUI since this is no longer required. You can find the proxy configuration in the Site System properties.
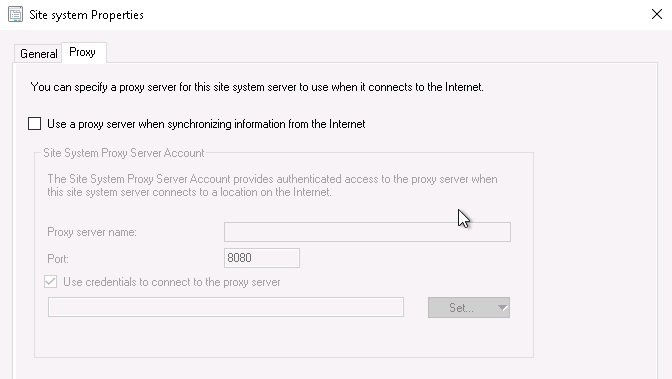
Once this has been removed, restart the ‘SMS_EXECUTIVE’ and ‘WSUS Service’ services. Finally test the downloading of SCUP updates, Windows Update Syncronisation and Windows Update downloads.
Hopefully everything works as expected now and you can get on with doing some meaningful work. It would be nice if Microsoft included options to bypass the web proxy in the GUI. There doesn’t appear to be any significant documentation from Microsoft on configuring the proxy bypass so we hope this information helps some people out.

